Your registration has been confirmed. Thank you for signing up!
When operations and security teams work together, companies can achieve complementary goals when it comes to monitoring and observability — surfacing business-critical information while ensuring compliance and end-user privacy. In this whitepaper, we’ll go over the five essential security features to look for in a monitoring and observability solution and how the right toolset can empower both security and operations teams.

Security and visibility — contrary to popular opinion — go hand in hand. When operations and security teams work together, companies can achieve complementary goals when it comes to monitoring and observability — surfacing business-critical information while ensuring compliance and end-user privacy.
Whether your concerns are around security and privacy in the public cloud or securing your Docker containers, it’s important to find a monitoring tool that meets certain criteria when it comes to security. In this whitepaper, we’ll go over the five essential security features to look for in a monitoring and observability solution and how the right toolset can empower both security and operations teams.
We’ll go into each feature below, or feel free to click ahead to the feature you’re most interested in learning about.
Because monitoring requires some degree of access to your systems, it’s important to have measures in place to ensure the right people are accessing your resources (and make sure they’re performing the appropriate actions on those resources). Role-based access control (RBAC) is one such measure. RBAC enables you to lock down access to resources based on roles; you assign a user to a particular role, which in turn dictates the actions they’re allowed to perform on a resource. To imagine how that might apply to monitoring, you might, for example, have an operator role — in order to perform their day-to-day job, they need to be able to create checks, so that capability is defined as part of their role. An auditor might need to see those checks — but not edit or create them — so that role would be defined with read-only privileges when it comes to checks.
At Sensu, we modeled our RBAC implementation after Kubernetes RBAC, and if you’re familiar with the concept of Kubernetes namespaces, the workflow and terms should look familiar: you’ll configure permissions via sensuctl or via the Sensu API, and top-level types are defined as Role, ClusterRole, RoleBinding, and ClusterRoleBinding. Here’s a brief breakdown of terms:
A Role is essentially a collection of permissions, which are only added, not denied. You can limit a role to a single namespace or cluster-wide with a ClusterRole. We’d recommend starting with the default ClusterRole in Sensu:
$ sensuctl cluster-role list
Name Rules
─────────────── ───────
admin 2
cluster-admin 1
edit 2
system:agent 1
system:user 2
view 1
You can associate permissions to a user or group of users with a binding. Grant permissions to a specific namespace with a RoleBinding, or cluster-wide with ClusterRoleBinding.
We recommend creating a test namespace to try out setting up roles. Once you have things set up as you like, you can integrate those roles into a production namespace.
RBAC resources:
As noted earlier, your monitoring tool requires some degree of access in order to serve its main function — giving you visibility into your applications and services. However, you want to avoid putting plaintext secrets (such as passwords and API keys) directly into your monitoring configurations, as that can open you up to security issues. And while those credentials are critical to your monitoring operations, you don’t want your monitoring tool to become an attack vector.
With secrets management, you’re able to safely and securely manage authentication credentials (AKA, “secrets”) in your infrastructure. Secrets management improves monitoring and observability in three major ways:
Sensu secrets management works with HashiCorp Vault or any provider of your choosing via our environment variable, including Google Cloud Secrets Manager, AWS Secures Manager, Azure Key Vault, Kubernetes Secrets, CyberArk, and more.

As noted above, Sensu integrates directly with HashiCorp Vault, supporting both the token authentication and certificate authent ication methods in Vault.
Here’s how your Sensu configuration with HashiCorp Vault secrets might look:
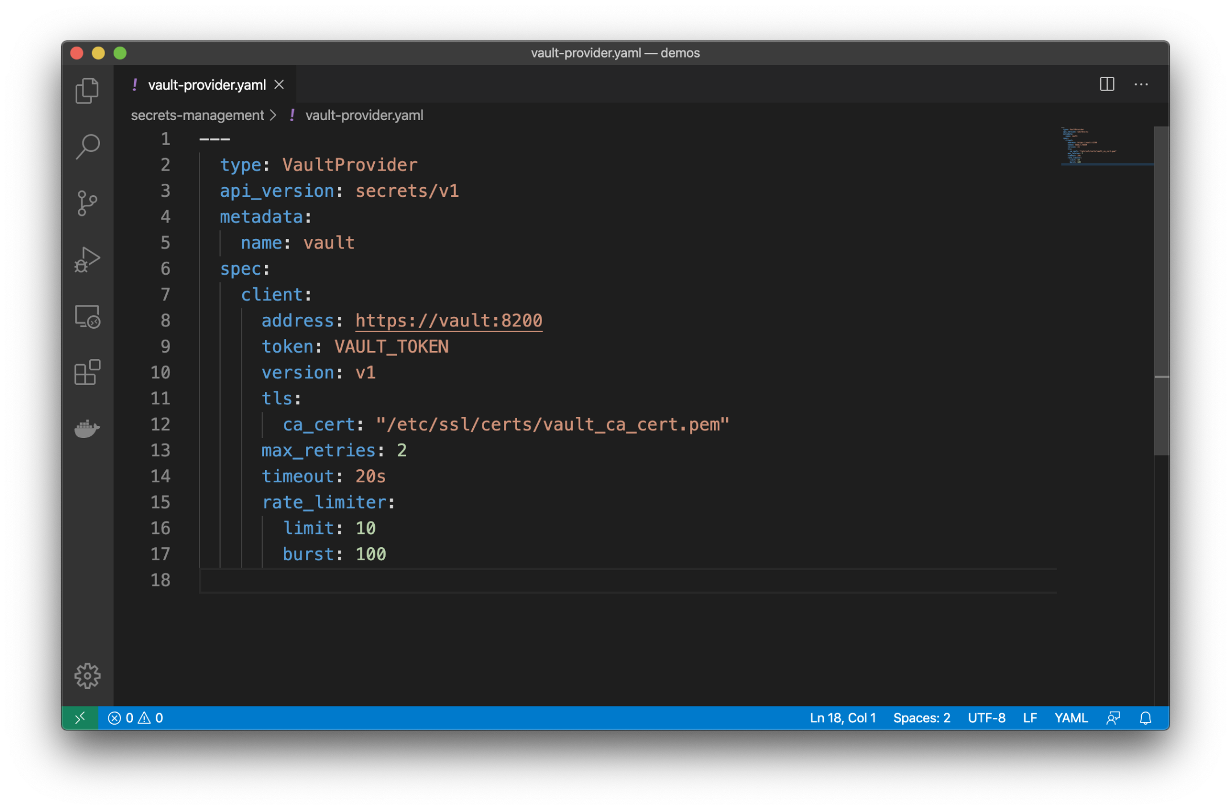
Secrets management resources:
Single sign-on (SSO) enables users to sign into various different services via a single username and password. By using SSO with your monitoring tool, you can make it easier for the right users to access your monitoring data and workflows. By choosing a solution that works with existing, industry-standard single sign-on solutions, you can ensure smooth workflows across your whole organization.
Sensu integrates with enterprise single sign-on solutions like Azure Active Directory, Google Cloud Identity, Okta, PingIdentity, Auth0, OneLogin, and more.

Users need a username and password in order to access the Sensu web UI, API, and sensuctl, the Sensu command-line tool. You can set up user login either via Sensu’s built-in authentication and RBAC or via one of the aforementioned authentication providers, as well as Lightweight Directory Access Protocol (LDAP) tools.
Sensu makes it easy to view and manage your SSO tools; to view your current active authentication providers, for example, you’d enter the following command:
sensuctl auth list
Check out our documentation to learn more about how to configure authentication access to Sensu.
Mutual TLS (mTLS) authentication — also known as two-way authentication — enables two entities to authenticate to each other at the same time. Like transport layer security (TLS), mTLS provides encrypted communications but, instead of a client authenticating to a server by means of a trusted Certificate Authority (CA), a server authenticates to another server using mTLS, also through a mutually trusted CA.
Both mTLS and TLS are critical to protecting network communications from eavesdropping and man-in-the-middle attacks. As noted earlier, it’s critical that your monitoring not become an attack vector; by using secure protocols like mTLS and TLS, you can ensure your monitoring remains secure.
mTLS allows the Sensu agent to authenticate to the backend without requiring usernames and passwords. mTLS is also a requirement to take advantage of Sensu secrets management. And, Sensu works with industry-standard PKI and CRL providers like Red Hat Certificate System, AWS Certificate Manager, HashiCorp PKI Secrets Engine, and more.

For more on mTLS with Sensu, check out our documentation on Sensu agent mTLS authentication.
No two organizations are exactly alike, and as such security requirements are certain to differ. In addition to the afore-mentioned table-stakes features required for a secure monitoring solution, it’s important to find a tool that gives you the flexibility to integrate with the tools you’re already using. Sensu offers an array of integrations for cloud monitoring, which includes the security tools that make up your DevSecOps stack.
One such example is integrating a popular intrusion detection system (IDS) like Tripwire with your monitoring. An IDS will monitor and alert on changes to your file system (AKA, it uses file integrity checking to make sure key files haven’t been altered). By integrating an IDS like Tripwire with your monitoring, you can fine-tune alerts to cut down on false positives and alert fatigue.
An IDS is just one example of a security integration for monitoring. Due to Sensu’s flexibility and dynamic runtime assets, you’re able to integrate with just about anything you need as part of your security infrastructure. And with Bonsai, the Sensu asset index, you’re able to search for and create your own integrations for monitoring.
We hope this guide gives you some idea of what to look for when it comes to finding a secure monitoring solution. Check out the related resources below, and thanks for reading!