The following is a contributed post from Chima Mmeje. She is a content strategist who helps SaaS and tech brands build topic clusters and execute their content strategy.
As corporations grow, the need to organize user data and assets into a hierarchical structure becomes critical to simplify storage access of those assets. LDAP enables organizations to store, manage, and secure information about the organization, its users, and assets.
In this guide, we’ll explain what LDAP is, its uses, and how it works. We’ll also discuss the levels of LDAP directory and data components – illustrating how it’s an essential tool for managing data about organizations and users alike.

What Is Lightweight Directory Access Protocol (LDAP)?
LDAP is a lightweight version of the Directory Access Protocol (DAP). Its original goal was to provide low-overhead access to an X.500 Directory, but the tool now has a wider variety of uses, which we will discuss later.
LDAP’s primary function is enabling users to find data about organizations, persons, and more. It accomplishes this goal by storing data in the LDAP directory and authenticating users to access the directory. It also provides the communication language that applications require to send and receive information from directory services.
Data and resources that you can find with LDAP include files and user information. It works with printers, computers, and other devices connected via the internet or a company’s intranet.
LDAP works with most vendor directory services, such as Active Directory (AD). With LDAP, sharing information about users, services, systems, networks, and applications from a directory service to other applications and services becomes easier to implement.
What Is LDAP Authentication?
A user cannot access information stored within an LDAP database or directory without first authenticating (proving they are who they say they are). The database typically contains user, group, and permission information and delivers requested information to connected applications.
LDAP authentication involves verifying provided usernames and passwords by connecting with a directory service that uses the LDAP protocol. Some directory-servers that use LDAP in this manner are OpenLDAP, MS Active Directory, and OpenDJ.
Here’s a step-by-step breakdown of the authentication process:
- The client (an LDAP-ready system or application) sends a request to access information stored within an LDAP database.
- The client provides their LDAP server user credentials (username and password).
- The LDAP server cross-checks the user’s submitted credentials against the core user identity data stored in its LDAP database.
- If the provided credentials match the stored core user identity, the client can access the requested information.
- Incorrect credentials will lead to denied access to the LDAP database.
Note that the core user identity stored in the LDAP database isn’t necessarily just usernames and passwords, but also other attributes like addresses, telephone numbers, and group associations.
LDAP vs Active Directory
Active Directory (AD) was developed by Microsoft for Windows domain networks. It is included as a set of services and processes in most Windows operating systems and contains information about each user account connected to the network.
LDAP is a tool for extracting and editing data stored in Active Directory and other compatible directory service providers. Each user account in an AD has several attributes, such as the user’s full name and email address. Extracting this information in a usable format requires LDAP.
LDAP extracts information from AD with a simple, string-based query. LDAP can also share the extracted information (such as usernames and passwords) with connected devices or applications.
Using LDAP eliminates the need for users to manually enter a string of LDAP queries to retrieve information from AD. For example, Microsoft Outlook is an LDAP-enabled Windows program that enters queries automatically to get you the information you want.
What is LDAP used for?
Since LDAP is an open and cross-platform protocol, it works with several directory service providers and has various applications. The most common LDAP use case is serving as a central location for storing authentication information, such as usernames and passwords. You can use the stored authentication information on various applications to validate users.
Popular applications that support LDAP authentication are OpenVPN, Docker, Jenkins, Kubernetes, and Linux Samba servers. System administrators also use LDAP’s single sign on (SSO) feature to manage LDAP database access.
LDAP Operation Types
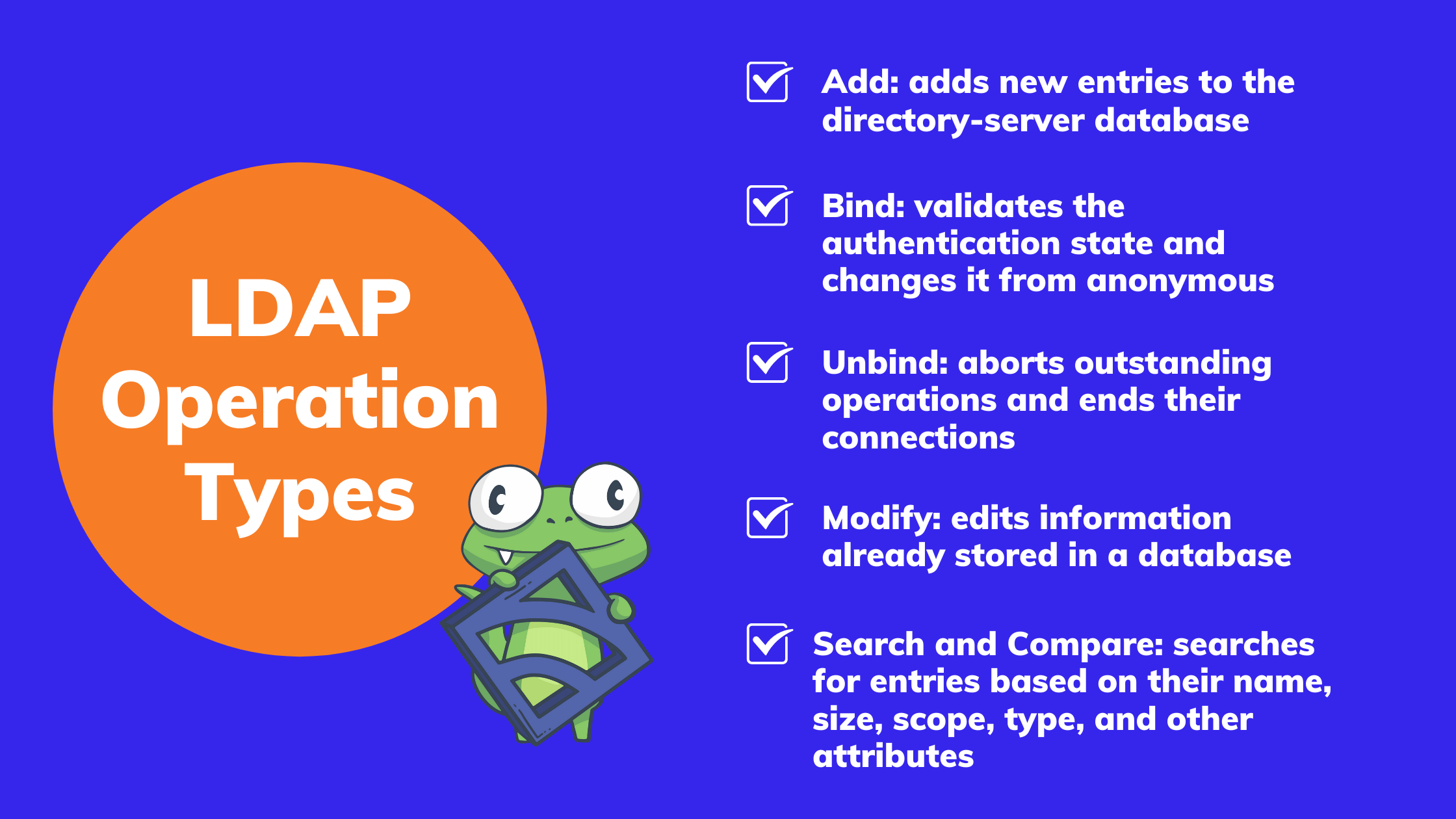
Here are some basic types of operations in LDAP:
Add
The feature allows you to add new entries to the directory-server database. If the added name already exists, the server won’t accept the entry. Instead, it will deliver an “entryAlreadyExists” notification. LDAP-compliant servers will store added names and other attributes according to the prescribed naming standards to ensure uniformity.
Bind (Authentication)
When you create a session by connecting to an LDAP server, the session’s default authentication state is anonymous. The LDAP bind feature validates the authentication state and changes it from anonymous. Bind can occur either through the Simple or SASL (Simple Authentication and Security Layer) authentication method.
Unbind
Unbind aborts outstanding operations and ends their connections. You can accomplish the same thing by closing the connection, but using unbind is preferred because it frees up resources that may remain assigned to the aborted operation.
Modify
LDAP clients use the modify feature to edit information already stored in a database. Only three types of modifications are permissible:
- Adding a new value to the data
- Replacing or overwriting an existing value
- Deleting an existing value
Search and Compare
The operation lets clients search for and read entries. You can search for entries based on their name, size, scope, type, and other attributes. The compare feature makes it easy to verify whether a named entry has specific attributes.
Delete
Clients use this feature to delete entries from the directory. Note that deletion will not occur unless the client sends a perfectly composed delete request to the server. Some of the features the delete request must have are:
- The name of the entry you want to erase
- Attached request controls
Levels of LDAP Directory
A typical LDAP configuration follows a “tree” hierarchy format. Below are the hierarchy levels from start to end:
- The starting place – a root directory
- Countries
- Organizations or companies
- Divisions, departments, and other organizational units
- People, files, and shared resources (printers, computers, and so on)
You can distribute an LDAP directory across several servers. Queries from the clients are distributed across the multiple servers with the help of replication. Each LDAP server receives requests from users and takes responsibility for the requests before passing them to other servers. The servers will have a replicated version of the directory, and the directories will all synchronize their entries at regular intervals.
LDAP Data Components
Several components work together for LDAP to complete its myriad of tasks, especially when it comes to how it queries and displays data to users. The most essential of these components are:
Attributes
The actual data within an LDAP system are stored as attributes. Each attribute is associated with an attribute type that specifies how clients and the directory server should interact with that attribute. Also, attribute values contain most of the data that users store and access in LDAP systems.
Entries
Attributes define the characteristics of a user or item, while an entry describes the user or item by listing all of their attributes under a name. On their own, attributes have limited functions. You have to associate an attribute with an entry before you can fully utilize it.
Data Information Tree (DIT)
Within an LDAP system, the data defined by attributes represent only a fraction of an object’s available information. The remaining information is obtainable from the entry’s placement within the LDAP system and the relationships its placement suggests. For example, if you have an entry for “inventoryItems” and another for “people”, the data entered under each one will provide a better idea of what each entry represents.
Every entry in an LDAP system is set up as branches on Data Information Trees (DITs). Since every entry in an LDAP tree can symbolize almost anything, users mostly use entries for keeping things organized.
Schemas
Schema is a construct where related ObjectClasses and attribute definitions go under the same category. One DIT can have several unrelated schemas for generating the entries and attributes it needs.
Next steps and further learning
LDAP is an easy-to-implement protocol for consolidating information within your organization. It also serves as a central hub for authentication. You can collect and save user information under one LDAP directory. Whenever an LDAP-enabled application needs any of the stored information, it automatically queries the directory to retrieve it.
Another benefit is that LDAP is open source and compatible with various operating systems, including Windows and Unix-based systems. Below, we’ve included some resources and FAQs — including a blog post on how LDAP authentication works with Sensu Go.

FAQs
What is an LDAP server?
An LDAP server, also called a Directory System Agent (DSA), runs on Windows OS and Unix/Linux. It stores usernames, passwords, and other core user identities. It uses this data to authenticate users when it receives requests or queries and shares the requests with other DSAs. Several applications and services can connect to a server at once to validate users.
How does LDAP work?
LDAP is a cross-platform protocol for authenticating via directory services. It also provides the communication language applications use to connect to other directory service servers. These directory services house usernames, passwords, and computer accounts, and provide that information to users on the network upon request.
Picture LDAP as a huge virtual phone book. Opening the phone book gives you access to a large directory of contact information for various people, including their usernames and passwords. With LDAP, you can easily verify the credentials of users when they try to access your organization’s database.
What is an LDAP Account?
LDAP Account is an online application for managing different types of accounts stored in an LDAP directory. The account gives users an abstract view of a directory, which makes it easy for people who aren’t tech-savvy to manage LDAP data.
What is the difference between LDAP and Active Directory?
Active Directory (AD) is the directory service database used to store data, authentication and policy of an organization while LDAP is the protocol to communicate with the AD.
In summary, AD works with LDAP, and combining the two applications improves access management.
Is LDAP secure?
LDAP authentication provides standard security with an built-in layer of access management. Malicious actors may still eavesdrop during data transmission between Active Directory and clients. Optimize security by adding SSL/TLS encryption to the LDAP authentication process, which makes information transmitted during the authentication process less vulnerable by encrypting communications.
The default LDAP port used for authentication (Port 389) does not have its own security. Create a secure connection by adding security extensions, such as the LDAPv3 TLS extension or StartTLS mode.
How do you query in LDAP?
LDAP queries facilitate searching for computers, users, groups, and other objects within the Active Directory. LDAP extracts information from AD with the help of a simple, string-based query. You can also use utilities, such as ldapsearch, PowerShell, or VBS scripts to execute queries.
SAML vs LDAP
LDAP and SAML are both authentication protocols that help applications access IT resources. SAML sends user information to your identity provider and other online applications, while LDAP facilitates on-prem authentication and other server processes.
Most organizations combine the use of SAML, LDAP, and other authentication protocols to access various types of IT resources and achieve their business objectives.
Kerberos vs LDAP
Kerberos is a single sign-on and authentication protocol for managing credentials securely. It lets a process connect to an authentication server and provides signed and encrypted tickets for accessing files, applications, and other resources.
LDAP, on the other hand, facilitates accessing OpenLDAP, Active Directory, and other directories. It authenticates connections by cross-checking usernames and passwords stored in the LDAP directory. Since Kerberos is more secure than LDAP and LDAP has more functions than Kerberos, most organizations use both protocols.




